Published
- 4 min read
Quickly Prevent OS Command Injection in Palo Alto GlobalProtect Gateways

OS Command Injection Vulnerability in GlobalProtect Gateway (PAN-OS CVE-2024-3400)
Palo Alto Networks identified a critical vulnerability in its operating system widely used in network security appliances, PAN-OS. This vulnerability specifically impacts PAN-OS versions 10.2, 11.0, and 11.1.
The vulnerability CVE-2024-3400 could allow an attacker to execute arbitrary code remotely, potentially leading to unauthorized access, data breaches, and other malicious activities.
Summary: Quick Actions to Protect Impacted Systems
- Enable Threat ID 95187 in Palo Alto’s Threat Prevention. May need Troubleshooting.
- Check back for the patch on April 14, 2024.
- Disable Device Telemetry. (See Below)
Palo Alto Patch Status
Palo Alto intends to release a patch on April 14, 2024. Until then, Palo Alto recommends applying the steps below to mitigate the risk posed by CVE-2024-3400.
How to fix PAN-OS CVE-2024-3400, Palo Alto’s OS Command Injection Vulnerability
At the time of this article, Palo Alto has yet to release an official patch for the vulnerability. When the patch comes out, it will most likely be the best course of action. Until then, customers with a Threat Prevention subscription should enable Threat ID 95187.
However, there have been some issues noted when trying to apply the Threat ID 95187 ruleset.
Quick Guide to Apply Protection to GlobalProtect
There have been some issues noted when trying to apply the Threat ID 95187 ruleset. See below for potential solutions.
- Get Latest Content Update – Currently, 8833-8682 (released on 4/11/2024).
- Find Correct Zones for GP Portal and GP Gateway
- Determine the correct zone for GP portal and GP gateway by going to
Network > GlobalProtect > Portals - The associated zone for the GlobalProtect portal can be found in
Network > Interfaces > Ethernet - Find the gateway and associated interface by going to
Network > GlobalProtect > Gateways
- Determine the correct zone for GP portal and GP gateway by going to
- Modify or Create a New Vulnerability Protection Profile
- Option 1: Go to
Objects > Security Profiles > VulnerabilityProtection and set the blocking action of “reset-server” for all critical severity signature triggers. - Option 2: Add an exception specifically for the relevant signature (#95187 in this case) to configure the reset-server action for this signature when it triggers (see below).
- Option 1: Go to
- Create a Firewall Security Rule
- Go to
Policies > Securityand create a new policy- Source zone should be “any”.
- Destination zone is the GlobalProtect gateway and/or GlobalProtect portal zones found in the first stem.
- Assign the Vulnerability Protection Profile modified/created in step 2 to the rule.
- Go to
- Commit the Changes
For more guidance see Palo Alto’s Guide Applying Vulnerability Protection to GlobalProtect Interfaces.
Troubleshooting Applying Threat Prevention Threat ID 95187
The rule “Threat ID 95187” has been not showing up for some clients attempting to enable it when attempting to prevent CVE-2024-3400.
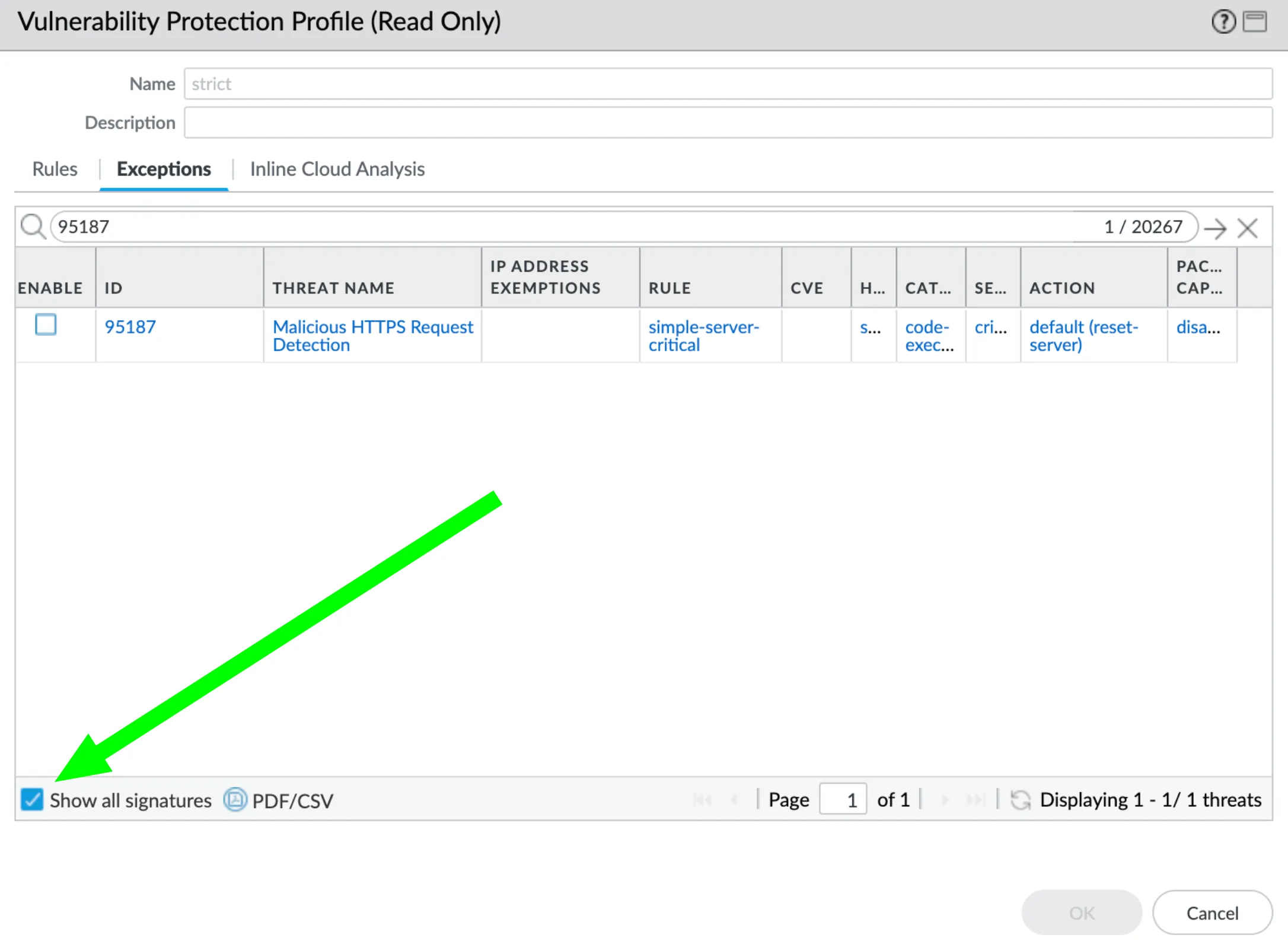
Below are some ways found to fix missing Threat ID 95187 if it is not showing up.
- Go to the exceptions tab and check show all signatures.
-
- Reverting the app and deleting 8833 then redownload and reinstall it to solve the problem.
- Note that reinstalling the application did not work for some users.
- To get the update to show the rule in the GUI one user clarified they ”
Installed 8833 through CLI after running a "request content upgrade check" by running "request content upgrade download latest " and then "request content upgrade install latest"”. - If threat ID 95187 is still not showing after installing the Applications and Threats content version 8833-8682, another suggestion was to log out and back in, open incognito mode, or restart the management server.
Disable Device Telemetry
Additionally, Palo Alto recommends disabling device telemetry until a patch is available. Device telemetry can be disabled by following the below steps:
- Navigate to: Device > Setup > Telemetry.
- Edit the Telemetry widget.
- Uncheck the Enable Telemetry box.
- Click OK and then commit your changes.
For more information see Palo Alto’s Guide on Disabling Device Telemetry.
Sources:
- Palo Alto’s Networks Security Advisory: CVE-2024-3400 PAN-OS: OS Command Injection Vulnerability in GlobalProtect Gateway
- Palo Alto’s Guide on applying vulnerability protection to GlobalProtect Interfaces: https://live.paloaltonetworks.com/t5/globalprotect-articles/applying-vulnerability-protection-to-globalprotect-interfaces/ta-p/340184
- CISA News: https://www.cisa.gov/news-events/alerts/2024/04/12/palo-alto-networks-releases-guidance-vulnerability-pan-os-cve-2024-3400
- NIST’s National Vulnerability Database Listing: https://nvd.nist.gov/vuln/detail/CVE-2024-3400
- Palo Alto’s older guidance on Missing Threat ID in the exception tab of Vulnerability Protection Profile on WebGUI: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g0000008U27CAE